Still Running Your Business on a Terminal or Legacy Backend?
We help established companies safely modernize terminal-based and legacy backend systems into secure, modern web platforms—without downtime, data loss, or operational chaos.
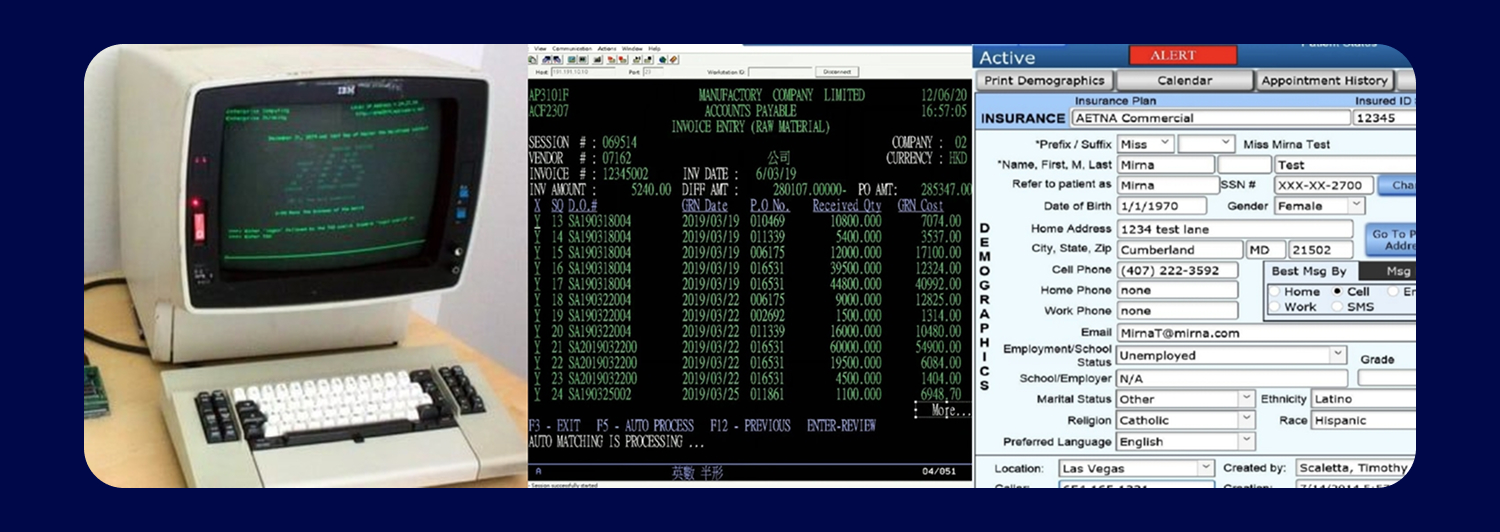
If This is How Your Business Still Accesses Critical Data…
You're Not Alone. This Is Fixable.
If you're here because:
Your only developer who understands the system just announced their retirement
Your business runs on software that only 1-2 people know how to maintain
You're being told to "use AI" but your data is locked in a terminal system
Off-the-shelf ERP platforms can't handle your complex operations
...then you're in the right place.
We've modernized legacy systems for manufacturers, distributors, and service companies across Metro Detroit. Your situation isn't unique—and it doesn't require starting over.
The Risk Isn’t the Technology — It’s the Dependency
Many established businesses aren’t held back by outdated software — they’re exposed by how much of their operation depends on it.
Over time, legacy systems quietly become single points of failure. Not because they stop working, but because fewer and fewer people truly understand how they work, how to change them, or how to recover when something goes wrong.
What once felt stable can quickly become fragile.
Where the Risk Shows Up
Core systems rely on tribal knowledge - Business logic lives in people’s heads, not documentation.
One or two people truly understand how things work - If they retire, leave, or become unavailable, the business is exposed.
Reporting is slow, manual, or brittle - Data exists, but extracting it requires workarounds, exports, or custom scripts.
Security, auditability, and access controls are limited - Legacy systems weren’t designed for modern security expectations.
Your data is inaccessible to modern tools — including AI - Valuable operational data is locked behind terminal screens and custom workflows.
Most Companies Don’t Realize How Exposed They Are
If the system still works, it feels safe — until it doesn’t.
The risk isn’t that the system will fail tomorrow.
It’s that when something changes — people, regulations, security requirements, customer expectations — the business can’t adapt without significant disruption.
That’s the moment legacy systems stop being an inconvenience and start becoming a liability.
Why Legacy Systems Stay in Place for Decades
Most modernization efforts are delayed not because leaders don’t see the issue — but because the perceived risk of disruption feels greater than the known risk of staying put.
When a system runs core operations, even imperfectly, stability becomes the priority. Over time, the business adapts around the limitations. Workarounds form. Knowledge concentrates. The system becomes untouchable — not because it’s ideal, but because the cost of getting it wrong feels too high.

The Common Fears We Hear
“We can’t afford downtime.” Any disruption to daily operations feels unacceptable.
“No one fully understands the system anymore.” The original logic exists, but the documentation doesn’t.
“A rewrite would be too risky." Starting over sounds more dangerous than living with the current state.
“We’ll deal with it later." As long as things keep working, modernization stays off the critical path.
These concerns are rational. They’re also the reason legacy systems tend to remain untouched far longer than they should.
Unfortunately, modernization is rarely optional — it’s just postponed until it’s forced by people, security, compliance, or growth.
How We Modernize Legacy Systems—Without Breaking the Business
Modernizing a legacy backend doesn’t require starting over or putting daily operations at risk. The goal is to make progress without disrupting what already works.
Our approach focuses on understanding the existing system first, then modernizing access to it in controlled, measurable steps.
Our Approach
This Is Not a “Rip and Replace” Project
Legacy modernization works best when it’s incremental. Systems often run in parallel during the transition, reducing risk and maintaining operational continuity. The business keeps moving while modernization happens quietly in the background.
We start by learning how the system is actually used day to day — not just how it was originally designed. This includes data flows, business rules, and operational dependencies.
Data is accessed and migrated in phases, allowing critical systems to continue running while visibility and security improve over time.
Years of embedded logic aren’t discarded. We retain what works and make it accessible through modern, maintainable interfaces.
Terminal-based processes are progressively replaced with a secure, role-based web application designed for real users — not IT specialists.
Once data is accessible, modern reporting, integrations, and AI-driven capabilities become possible without reworking the core system again.
1. Analyze the existing system and workflows
2. Secure and extract data incrementally
3. Preserve business logic while modernizing access
4. Replace terminal workflows with a secure web application
5. Enable modern reporting, integrations, and AI readiness
Current Project Spotlight: Modernizing a 40-Year-Old Backend System
A real-world example of how we modernize legacy systems incrementally — without disrupting operations.
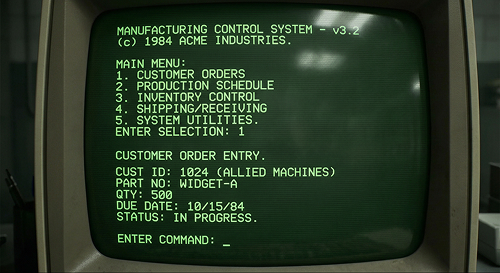
Terminal-Based Legacy System
DL4 terminal-only access
Decades of operational data
Knowledge concentrated in a few individuals
Critical systems, limited visibility

Secure Data Foundation
CSV data securely ingested into PostgreSQL
ETL pipelines inside a locked-down AWS environment
Natural-language access via a RAG web application
Data accessible in seconds — not screens
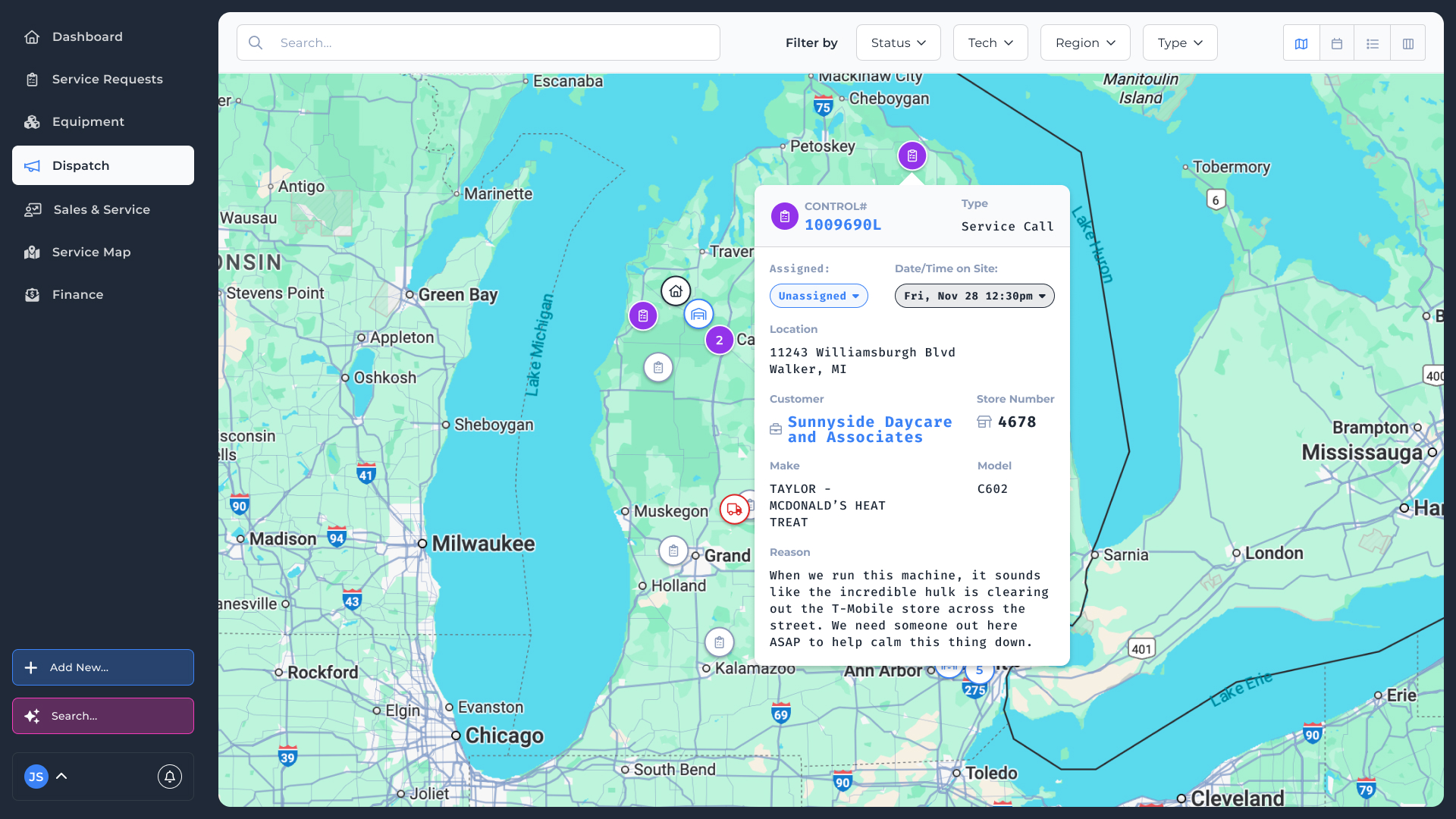
Modern ERP Platform (In Progress)
Custom ERP for dispatch, accounting, CRM, and job management
Role-based web access with encryption and auditability
AI-ready architecture built on clean, accessible data
Scalable, secure, future-proof
What We’re Doing
Rather than replacing the system outright, we’re modernizing access to it in phases.
This includes securely migrating and structuring historical data, preserving existing business rules, and introducing a modern web-based interface that replaces terminal workflows without interrupting operations. The new interface provides role-based access, improved security, and visibility into data that was previously difficult to reach.
At the same time, we’re preparing the system for future use cases — including modern reporting, integrations, and AI-driven capabilities — once the data is accessible in a usable format.
Why It Matters
By modernizing incrementally, the business reduces its dependence on a shrinking pool of system knowledge while maintaining operational continuity.
The result is lower operational risk, better visibility into the data that runs the business, and a foundation that can scale — without forcing a disruptive rewrite or abandoning decades of institutional knowledge.
Why Legacy Modernization Is Becoming Urgent
For many established companies, legacy systems have been stable for years. What’s changing isn’t the software itself — it’s the environment around it.
External expectations are shifting, and systems that once felt “good enough” are increasingly out of step with how modern businesses are expected to operate.
Retirement of system owners - The people who understand how these systems work are approaching retirement, with little opportunity to replace that knowledge.
Increasing security and insurance requirements - Cyber insurance, audits, and compliance standards continue to tighten, and legacy systems often struggle to meet modern expectations.
Leadership pressure to “use AI” - Executives are being asked to explore AI, automation, and advanced analytics — all of which depend on accessible, structured data.
Customer expectations for portals and access - Customers increasingly expect self-service, visibility, and digital access that legacy systems were never designed to support.
PE and board-level scrutiny - Investors and boards are paying closer attention to operational risk, system dependency, and scalability.
None of these pressures require immediate action on their own. Together, they make waiting more costly — and modernization harder — the longer it’s delayed.

What You'll Get Out of the Technical Discovery
An honest technical review designed to determine whether your legacy systems are becoming an operational or security risk—and what realistic, clear recommendations exist.
Identified single points of failure
Clear technical risk score
Modernization roadmap with phases & estimates
Security & continuity prioritization
No obligation to proceed.
Why Work With Moonello
Modernizing legacy systems requires more than technical skill — it requires judgment, restraint, and respect for how the business actually operates.
Our work is led by engineers who have experience modernizing real operational systems, not theoretical platforms. We focus on understanding how the system is used today, preserving what works, and reducing risk at every step.
Engineers, not consultants - You work directly with the people designing and building the system — not intermediaries or slide decks.
Experience with real operational systems - We’ve modernized systems that businesses depend on daily, where downtime and mistakes aren’t acceptable.
Incremental, risk-aware approach - Modernization happens in controlled phases, maintaining continuity while reducing dependency and exposure.
AI-assisted development to reduce timelines and cost - We use AI internally to accelerate development and testing, helping projects move faster while keeping budgets grounded.
Common Questions
Book a Technical Discovery & Modernization Plan
If your business depends on systems that only 1-2 people understand, let's talk. We'll assess your exposure and give you honest options—no sales pitch. We'll identify single points of failure, a clear technical risk score, a modernization roadmap with phases & timelines, and security & continuity prioritization.
No obligation to proceed. Engineers, not consultants.